My give back to the community initiative that was presented for free at several private and public events across Australia:
- Sydney - PlatypusCon (2017)
- Perth - BsidesPerth (2017)
- Brisbane - CrikeyCon (2018)
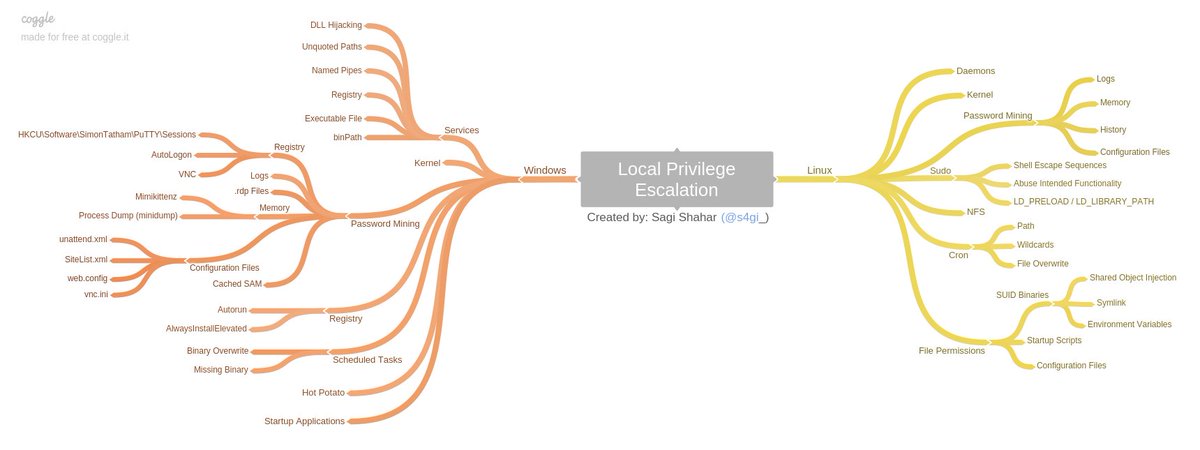
The workshop is based on the attack tree below, which covers all known (at the time) attack vectors of local user privilege escalation on both Linux and Windows operating systems.
- Workshop Slide Deck
- Exercise Worksheets (Linux, Windows)
- Lab VM for Linux Exercises (user:password321, root:password123)
- Kali VM for Linux/Windows Exercises (root:toor)
- Videos for Windows Exercises
- Tools for Windows Exercises (7z archive password: lpeworkshop)
- Windows exercises setup script
- Start a Windows VM that you legitimately own
- Login to the Windows VM using a user account that has administrator privileges
- Ensure the Windows VM does not have a user account named 'user'. If it exists, delete it
- Copy the setup script (lpe_windows_setup.bat) to a writeable location on a Windows VM (the Desktop directory is fine)
- Right click on the copied setup file and ensure to select from the pop-up menu 'run as Administrator'
- Read carefully the output of the script
- Restart the Windows VM
- Copy the Tools 7z archive to the Desktop and extract it
- Setup is now complete, enjoy
The script was developed and tested on a Windows 7 (SP1) x64 Build 7601 English-US host. It might work on other OS instances, but it is not guaranteed. Pay attention to the script's output. Some exercises are skipped (e.g. Kernel, etc.) as it depends on the patchlevel of the VM.
NOTE: As with any intentionally vulnerable hosts, ensure the Windows VM is not connected to an externally facing network.